The Wrong Question
82% of German enterprises want independence from US cloud providers, according to Bitkom's 2025 Cloud Monitor. Most assume the path is migrating to European infrastructure.
In June 2025, Microsoft's legal director confirmed in the French Parliament what legal teams already suspected: US providers cannot guarantee EU data protection from US government access. The CLOUD Act grants US authorities power to demand data from American companies "regardless of whether such communication, record, or other information is located within or outside of the United States."
AWS European Sovereign Cloud, Azure EU Data Boundary, Google Sovereign Cloud: different marketing, same legal reality. German subsidiary, EU staff, EU encryption keys—none changes the parent company's jurisdiction. Amazon.com Inc., Microsoft Corp., Alphabet Inc. are US corporations. CLOUD Act applies to all of them.
70% of European cloud infrastructure operates under a legal framework EU regulators cannot override. The dependence is structural, not contractual.
The conversation is stuck in a false binary: accept CLOUD Act exposure with US hyperscalers, or migrate to OVHcloud and lose capabilities.
Neither fully solves the problem.
The Custody Framework
Location alone doesn't determine sovereignty. Custody and location does.

EU providers solve jurisdiction. On OVHcloud, US law doesn't apply. French courts can compel OVH; German courts can compel Hetzner. That's rule-of-law operating as designed, and it eliminates US jurisdiction risk entirely.
But for organizations requiring zero provider custody—defense contractors, sensitive IP, regulated entities with strict data handling—even EU custody creates a vector. The only architecture that eliminates provider custody: you run the infrastructure, you hold the keys, no provider has anything to hand over.
The Non-Custody Architecture
Akave Inc. is a US company. Delaware. We face the same CLOUD Act legal framework as Microsoft, Amazon, and Google. We won't pretend otherwise.
But the architecture solves what corporate structure cannot.
In contrast to hyperscalers, Akave allows you to run a part of the software stack where you need it the most.
The self-Hosted O3, Akave's self-managed S3-compatible gateway, inverts the custody model. You run your own gateway on EU infrastructure—Hetzner, OVH, your data center. You generate and hold the encryption keys. Akave provides the protocol, the tools, the decentralized storage network. Encrypted shards distribute across geofenced nodes—restricted to EU if you choose—ensuring no single point of failure and no single jurisdiction holding a complete file.
We never have custody of decryption keys or readable data in this model. At most, we see encrypted fragments we cannot decrypt. The architecture ensures we never control decryption keys or readable content. You can't be compelled to produce what you never held in usable form.
What about malicious updates? Could a state actor compel Akave to push a compromised O3 gateway that exfiltrates keys? Possible in theory. That's why O3 builds are reproducible and auditable, and you control your update cadence. Audit every release before deployment. Air-gapped environments can run verified builds indefinitely.
Four properties make this distinct:
1. Client-Side Encryption with Customer-Held Keys
Data encrypts before leaving your gateway infrastructure. Keys never touch the Akave storage infra. Even if we received a CLOUD Act request, we'd have nothing to provide but encrypted fragments we cannot decrypt.
2. Reproducible, Auditable Builds
You verify exactly what runs on your infrastructure. No black-box binaries, no blind trust required.
3. Blockchain Audit Trail
Every access event logs onchain. Onchain records are immutable and third-party verifiable. A gag order might prevent us from notifying you about a request—but it can't erase what's already on a blockchain. Your regulators verify access patterns independently via a block explorer.
4. S3 Compatibility with Zero Lock-In
Full S3 API parity means you're never trapped. Migration is a DNS flip and an rclone sync - not a nine-month refactor. Zero egress fees mean you'll never pay a ransom to leave.
The Cost Reality
Sovereignty doesn't require premium pricing.
Scenario: 50TB storage, 100TB data movement, 12 months, EU deployment.
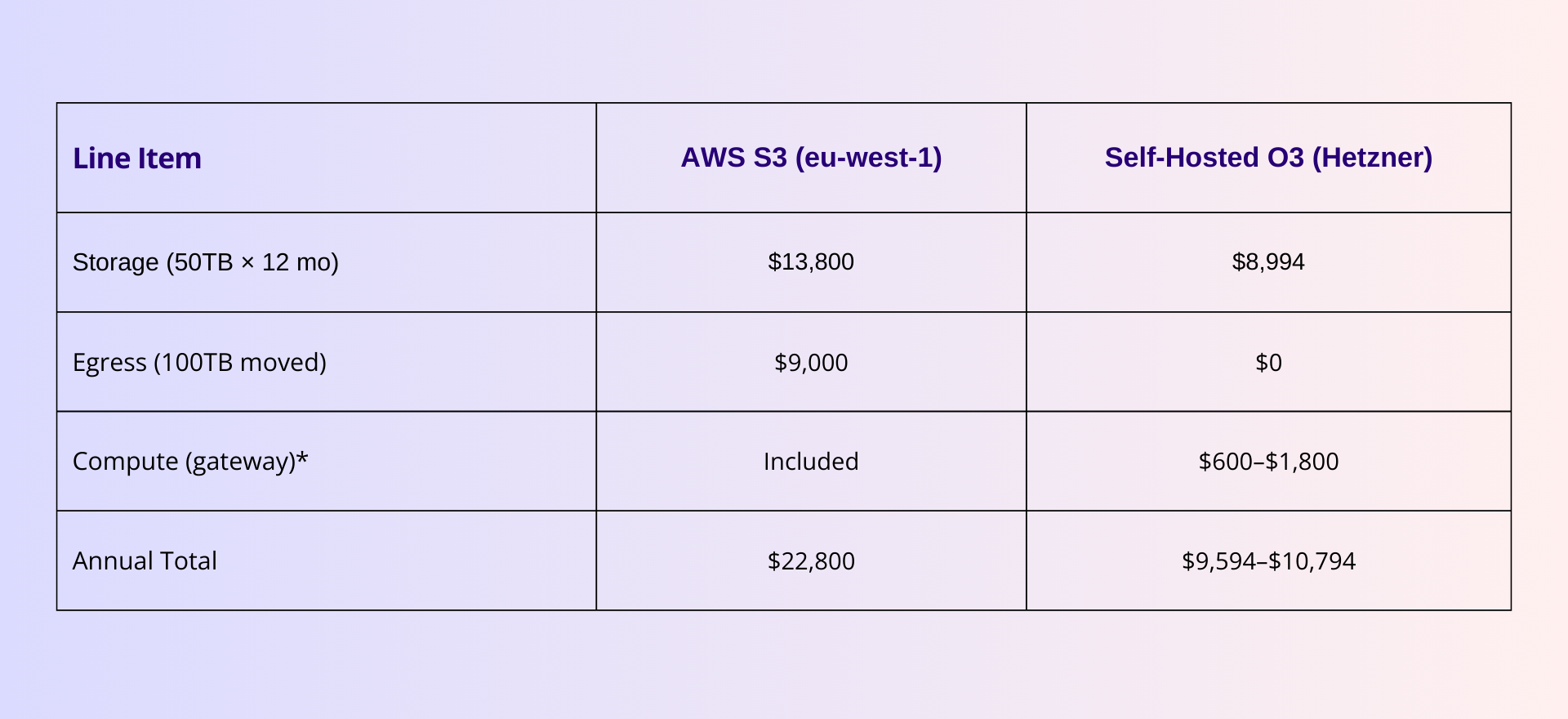
*Single gateway ~$600/year. Production HA (2-3 gateways) ~$1,200-1,800/year.
Savings: $12,000–$13,200 (52-58%)—plus meaningful sovereignty.
The $9,000 egress gap isn't a bug. It's the business model. Upload is free. Download costs $0.09/GB. The asymmetry is deliberate: if leaving costs more than staying, you stay.
Self-Hosted O3 kills that meter. No egress fees means migration freedom. Sovereignty isn't just legal jurisdiction; it's economic freedom to leave.
Compliance Reality
DORA went live January 2025. NIS2 enforcement is imminent. Both push firms to reduce single-provider concentration and third-country legal risk.
For organizations that need the strongest position, a non-custodial architecture is the most robust response we've found. DORA mandates that financial entities maintain a viable exit strategy. High egress fees are soft lock-in that regulators are flagging. With Self-Hosted O3, your exit strategy is built-in: zero fees to leave, ever.
When your auditor asks "Can a foreign government compel access to this data?" or "Can you migrate if needed?"—your answer changes from "It's complicated" to "For readable data: no" and "Yes."
Prove It
Deploy Self-Hosted O3 on a Hetzner VM. Run your own gateway. Generate your own keys.
You'll see Akave never touches your unencrypted data. You'll see access logs on-chain, immutable. You'll see S3 compatibility is real, not marketing.
Self-hosted means you own the ops. For teams without infrastructure expertise, Akave Cloud (managed) may fit better—with the tradeoff of provider custody. But if you need the most credible answer to CLOUD Act exposure, now you have it.
Deploy Self-Hosted O3 → | Calculate Your Savings →
Connect with Us
Akave Cloud is an enterprise-grade, distributed and scalable object storage designed for large-scale datasets in AI, analytics, and enterprise pipelines. It offers S3 object compatibility, cryptographic verifiability, immutable audit trails, and SDKs for agentic agents; all with zero egress fees and no vendor lock-in saving up to 80% on storage costs vs. hyperscalers.
Akave Cloud works with a wide ecosystem of partners operating hundreds of petabytes of capacity, enabling deployments across multiple countries and powering sovereign data infrastructure. The stack is also pre-qualified with key enterprise apps such as Snowflake and others.





