The Legacy of Traditional CIDs
Content Identifiers (CIDs), like those used in IPFS or Filecoin, revolutionized content addressing by tying identity to data itself rather than its location. These hash-based references made data sharing more reliable and decentralized systems more robust.
But in today’s high-stakes digital environment, traditional CIDs fall short. They reference raw data; untouched, unprotected, and vulnerable to unauthorized replication, tampering, or reverse-engineering.
Why Akave’s eCID?
Traditional CIDs (Content Identifiers), are calculated based on raw content. They offer a hash-based reference to the unaltered bytes of a file; simple, deterministic, and widely adopted.
But Akave’s CID is fundamentally different. Before a hash is calculated, the data goes through a transformative pipeline:
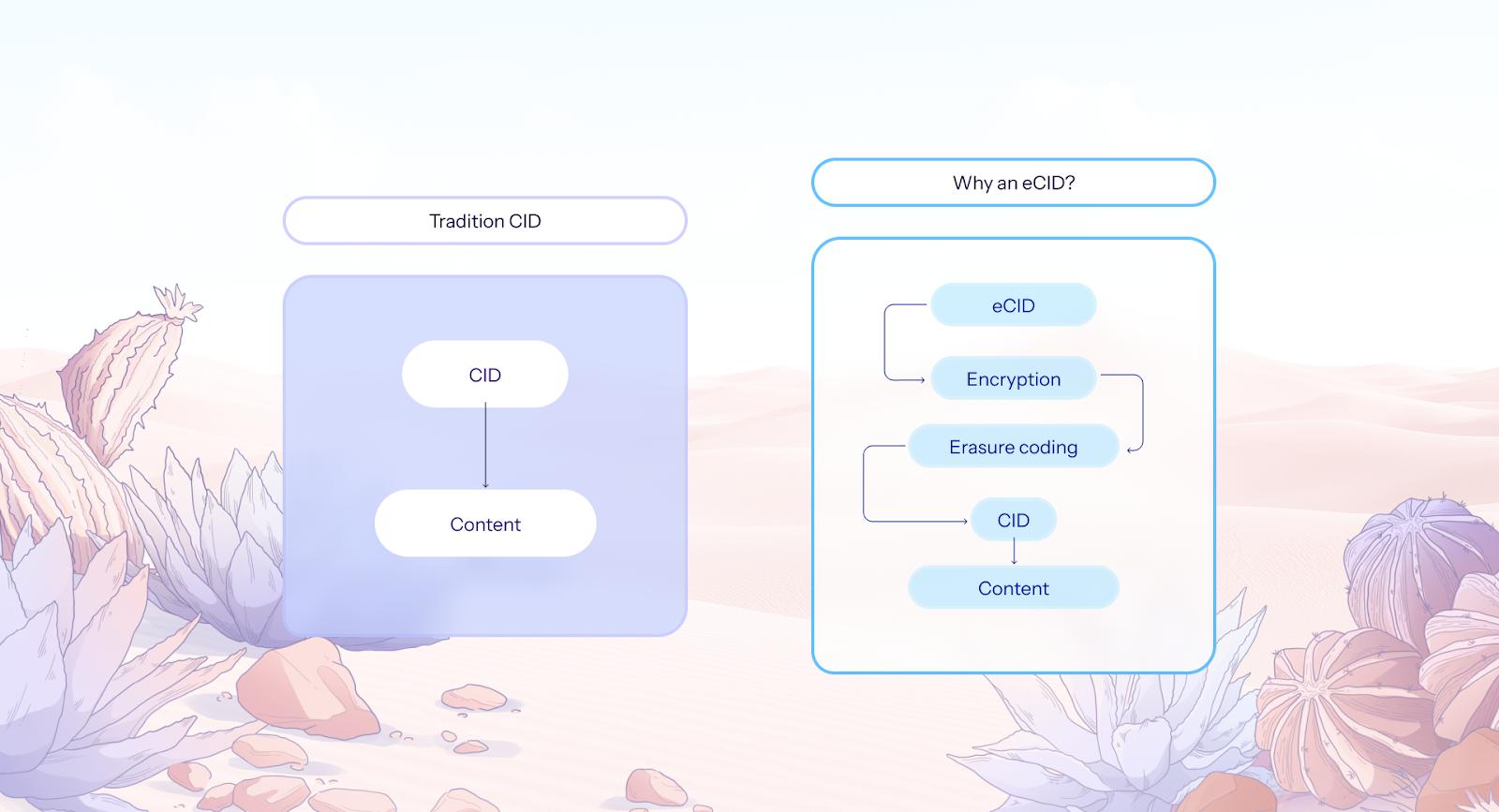
- Encryption: All data is encrypted by default, ensuring confidentiality.
- Erasure Coding: Data is split and encoded into multiple redundant chunks for durability and fault tolerance.
- Commit: Only after these steps does the final hash get calculated, making the CID refer not to the original data, but to a transformed, (e)ncoded CID.
Why the “e” Matters
The “e” in eCID signals a key distinction:
- It is not a direct hash of the user’s raw content.
- It represents the encoded form of the data, post-transformation but pre-commit.
This encoding guarantees security, verifiability, and recoverability at the protocol layer; something no traditional CID alone ensures.
Enterprise Implications
In regulated industries and enterprise infrastructure, Akave’s eCID model solves several critical problems that legacy content addressing cannot:
Cybersecurity & Ransomware Defense
Data encrypted by default makes unauthorized access nearly impossible; even if storage layers are compromised. Combined with erasure coding, eCID helps prevent exfiltration and ensures ransomware recovery paths are always available.
Tamper-Proof Guarantees
Because the CID is based on encoded, encrypted content, any modification; malicious or accidental; invalidates the eCID. This delivers a verifiable, immutable audit trail ideal for compliance-heavy sectors like finance, healthcare, and defense.
Malware Resistance
Traditional file systems and cloud object stores are susceptible to poisoned files, zero-day backdoors, or improper replication. Akave’s pipeline ensures that before any object is committed, it has passed a secure transformational stage; neutralizing many forms of embedded malware.
Data Lifecycle Control
With eCID, enterprises can build policies around retention, access control, and audit logging; all tied directly into the identifier. This enables fine-grained controls across hybrid clouds, data meshes, and zero-trust architectures.
Final Thoughts
With the introduction of eCID, Akave sets a new standard for enterprise-grade content addressing; one that’s built from the ground up with security, durability, and verifiability in mind. In a world where trust in data is non-negotiable, Akave’s eCID is your protocol-layer guarantee.
Connect with Us
Akave Cloud is an enterprise-grade, distributed and scalable object storage designed for large-scale datasets in AI, analytics, and enterprise pipelines. It offers S3 object compatibility, cryptographic verifiability, immutable audit trails, and SDKs for agentic agents; all with zero egress fees and no vendor lock-in saving up to 80% on storage costs vs. hyperscalers.
Akave Cloud works with a wide ecosystem of partners operating hundreds of petabytes of capacity, enabling deployments across multiple countries and powering sovereign data infrastructure. The stack is also pre-qualified with key enterprise apps such as Snowflake and others.






.webp)